For many years, car safety incidents have become the focus of public attention, mostly related to the theft of vehicles or the "crash" of engine control functions. For those automotive systems that are technically safe and reliable, these stories show us that they are unsatisfactory, and that risks are increasing as new threats emerge. During 2015-2020, the computing power in the car is expected to increase by a factor of 100. Hackers have also found more sophisticated ways to invade the car and control many functions, from broadcast to braking. Let's take a look at some of the challenges of designing a safe car and how to deal with them.
In the security field, people will talk about the attack surface of the system. A small attack surface means that there is no chance to invade, and a large attack surface means a lot of opportunities. In the past, intrusion into the car can only rely on attacking the lines inside the car, allowing them to mix into the messages exchanged between the electronic circuits (electronic control units) and create their own messages to attack the car.
A good example is if a criminal knows that there is a line through the underbody, there is a hole drilled there. They connected a probe to the line and used it to open the door and destroy its anti-theft system. This method works, but it is not scalable. However, there are a lot of expensive cars that have been stolen like this, and it is still the case!
More technology means increased attack surface
Look at the modern cars, and the ones that are being designed. They are distributed systems consisting of miles of lines. If you can reach them, there are many ways to invade the car. This explains why this problem is very thorny. Until recently, the only embedded radio station used was to provide keyless entry, but the automotive industry did not start well in this regard, as there are many examples of how to use signal boosters or to imitate.
There are even people who teach how to disrupt the in-vehicle infotainment system (IVI) via the FM Wireless Digital System (RDS). If there is a fake wireless source next to the car, it sends out an RDS jam message that the software should not receive, which can cause the embedded radio to crash. Of course, this is not a serious problem. It just makes us know that it is not easy to be safe, and it is not just a car.
All in all, it's not hard to see that the dramatic increase in wireless interfaces and software is a significant change for the automotive industry. Faced with these severe challenges, a lot of work has been done in the industry to solve it, and it will continue to be the main focus of industry attention.
The safe spell is "Don't trust anyone." With this in mind, designers must ensure that all vulnerabilities are blocked. Hackers can choose to attack from any point, and a loophole is enough. Charlie Miller gave a keynote speech at the recent ARM TechCon conference, letting us know how many vehicles are now vulnerable to hackers with sufficient technical knowledge and motivation.
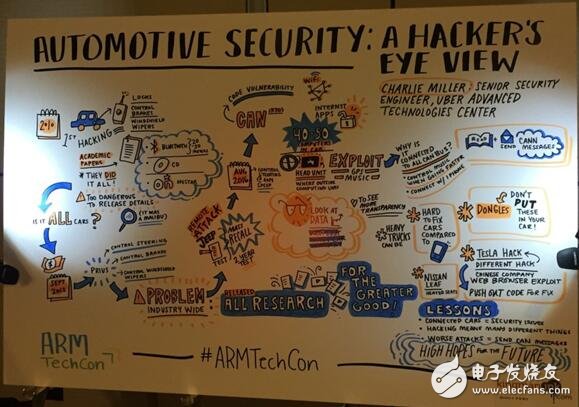
The main theme of Charlie Miller's ARM TechCon presentation
OTA (over-the-air) security
On the one hand, it is very important to build a car with a strong safety base, but it is imperative to solve them when problems arise. After all, problems always arise. A car usually lasts for more than a decade, and at that time it needs to be as safe as it is now. The key is to accept the fact that hackers can always find a way to invade, so we have to build a system that can and will be fixed. Currently, all automotive software is actually done through a cable line at a dealer or other authorized service agent, requiring reservations and labor costs. Everyone can see that this is not an expansive solution.
This means that the firmware OTA update (FOTA) is a very important endeavor to release security patches for automatic car downloads within a few days or even hours after the problem is discovered. Even if the problem of the car is very serious, the number of owners who are not willing to accept the recall is too scary.
In order to achieve scalability, it is necessary for automotive software to be repaired in an OTA manner.
The key to the success of OTA maintenance software is its ability to establish the credibility of the automotive network in a reliable manner. With a solid security foundation, the upgrade program does not actually have to interact with the compromised system. If the system is reliable, the identity information, credibility and manifest files of its software system can be verified. The car OTA system typically verifies these attributes of the system before authorizing the upgrade.
A hardware-based root of trust can be a solid foundation for FOTA because it can weigh a platform and interact with a remote OTA system (managed by the car manufacturer or its agents) in a secure manner. Software vendors have a real opportunity to develop this OTA connectivity and configuration framework.
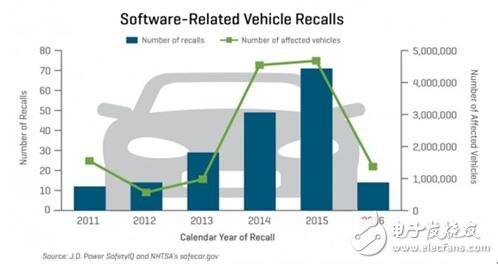
In order to achieve scalability, it is necessary for automotive software to be repaired in an OTA manner.
Another way to prevent attacks is through reporting. A loud car alarm can block a thief trying to get into the car. Some companies, such as TowerSec (now part of Harman), are developing systems that detect potential intrusions and find security concerns.
Car safety requires the efforts of all parties
As the supply chain in the industry continues to expand, building a safe car requires collaboration. The goal is to minimize the attack surface that can be exploited by hackers, and the smartphone industry has taken a long time to overcome this problem. Using a practical approach that has proven effective in this area, this will be a good starting point for the entire ecosystem to work on future car safety issues. Automakers can provide support by specifying and using software and hardware technologies, including:
· Hardware-based Trusted Execution Environment (TEE), such as ARM® TrustZone®-based GlobalPlatform TEE in application processors
· TrustZone-based uVisor in the microcontroller
· Security subsystems running in the Hardware Security Module (HSM), such as the ARM TrustZone CryptoCell
New standards for TEE management are also in the process of being developed, such as the recently announced Open Trust Protocol. It leverages PKI/CA and simplified TEE management to manage and ensure trust between all devices and service providers.
The mobile security architecture is moving toward low-cost MCUs (TrustZone for ARMv8-M and the recently released TrustZone CryptoCell-312 security IP for ARM), providing a real opportunity for the automotive industry to first attempt to establish a new level of hardware-based security.
Cars face many challenges in the future, and safety ranks first, but the industry still has time to make the right response. Automakers attach great importance to this issue by concentrating security technologies into centers of excellence through corporate restructuring, rather than spreading them around, or as an equity measure. ARM collaborates with partners throughout the supply chain to establish standards for security knowledge and security implementations designed to make next-generation cars safer.
WOODWORKING TOOLS
Get Great Discounted Prices on our range of woodworking tools
For your next project, whether at home or on the job, come to OPT's Woodworking Tools for all your need much much more!
You will find a wide selection of wood working tools.
We provide excellent support, and always try to answer your request within 1 day. This is not always possible, but we try our very best!
WOODWORKING TOOLS TYPE :
PCD Router Cutting Tools
Flexible in order quantity:
Samples can be provided before mass production, and MOQ can be discussed accordingly.
PRODUCT DETAIL:














PRODUCTING PROGRESS:
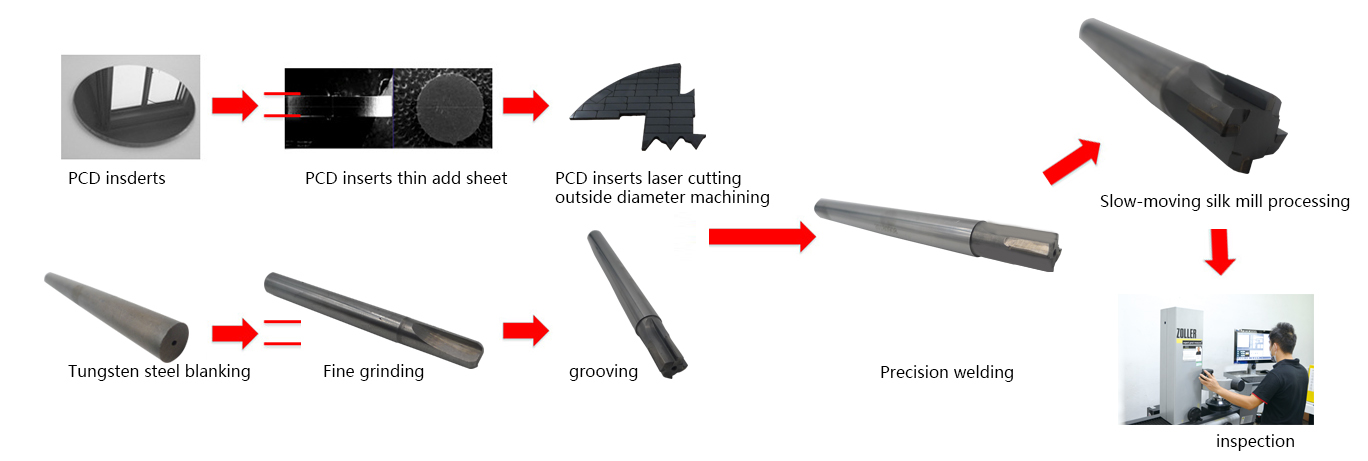
PAYMENT AND DELIVERY:

PRODUCT EQUIPMENT :

ABOUT US :
We are specialize in manufacturing PCD diamond tools and Carbide tools. Our major product inclulde PCD Inserts , PCD Reamers , PCD End Mills, PCD Taps, Cabide Inserts,Carbide Drills, Carbide Reams, Taps etc.,
We also offered customized cutting tools per drawings, and provide package according to customer requirements. We manufacture a series range of cutting tools for machining of Cast iron, Aluminium alloy and Non-Ferros metal, it is widely used in all major sectors like Automobiles, Engineering, Aerospace, Aviation and 3C industry. Premium quality of raw material is used in the production and strict examination during processing with advanced equipment, so our client are satisfied with our reliable quality and on-time delivery.
Our best selling of cutting tools include PCD Inserts, PCD End Mill, PCD Ball Nose Mill, PCD Reamer, Carbide Taps , Carbide End Mill, Special Form Cutter and many more. For these years we have been made a large forward in the technologies of manufacturing cutting tools. With high quality on performance and price, our product sells well both on domestic and overseas market. And we will always focus on the quality and best service, to make long business relationship.

quanlity control:
We have dedicated team of quality control and precise equipment to keep good and stable performance for our products and processing services.

Woodworking Tools,Router Bits,CNC Diamond Router Bits,Cnc Router Bits For Wood
OPT Cutting Tools Co., Ltd. , https://www.optdiamondtoolss.com
