1 Introduction
Network scanning is a technology based on the Internet that detects information on remote networks or hosts. It is also an indispensable means of ensuring system and network security. Host scanning refers to the security testing of the computer host or other network equipment to find out the security risks and system vulnerabilities. In general, both network scanning and host scanning can be classified as vulnerability scanning. Vulnerability scanning is essentially a double-edged sword: hackers use it to find ways to launch attacks on networks or systems, and system administrators use it to effectively prevent hackers from invading. Through vulnerability scanning, the scanner can discover the configuration information of the remote network or host, the allocation of TCP / UDP ports, the network services provided, and the specific information of the server.
2 Vulnerability scanning principle
Vulnerability scanning can be divided into five main technologies: ping scanning, port scanning, OS detection, vulnerability detection, and firewall scanning. Each technology achieves different goals and uses different principles. According to the structure of the TCP / IP protocol cluster, ping scanning works at the network layer: port scanning, firewall detection works at the transport layer; 0S detection and vulnerability detection works at the network layer, transport layer, and application layer. The ping scan determines the IP address of the target host, and the port scan detects ports opened by the target host, and then performs OS detection and vulnerability scanning based on the results of the port scan.
2.1 Ping scan
Ping scan refers to the scan that detects the IP address of the host. The purpose of ping scanning is to confirm whether the TCP / IP network of the target host is connected, that is, whether the scanned IP address is assigned to the host. For hackers without any predictive information, ping scanning is the first step in vulnerability scanning and intrusion; for network security personnel who already understand the overall IP division of the network, you can also use ping scanning to assign a host IP Precise positioning. In general, ping scanning is based on the ICMP protocol. The main idea is to construct an ICMP packet, send it to the target host, and judge from the response. According to the different construction of ICMP packets, it is divided into ECH0 scanning and non-ECHO scanning.
2.1.1 ECH0 scan
Send an ICMP ECHOREQUEST (ICMP type 8) packet to the target IP address and wait for UICMP ECHO REPLY (ICMP type 0). If ICMP ECHO REPLY is received, it means there is a host on the target IP, otherwise it means there is no host. It is worth noting that if the firewall on the target network is configured to block ICMP ECH0 traffic, the ECH0 scan cannot truly reflect the presence of hosts on the target IP.
In addition, if ICMPECHO REQUEST is sent to the broadcast address, the unix host on the network will respond to the request, and the windows host will not generate a response, which can also be used for OS detection.
2.1.2 Non-ECH0 scan
Send an ICMP TIMESTAMP REQUEST (ICMP type l3) or ICMP ADDRESS MASK REQUEST (ICMP type l7) packet to the destination IP address, and determine whether the destination host exists according to whether a response is received. When the firewall on the target network is configured to block ICMP ECH0 traffic, non.ECH0 scanning can be used for host detection.
2.2 Port scanning
Port scanning is used to detect the ports opened by the host. Port scanning usually only performs the simplest port connectivity test without further data analysis, so it is more suitable for a wide range of scans: scanning a specified port value segment for a specified IP address, or a specified port value Scan the address segment. According to the protocol used for port scanning, it is divided into TCP scanning and UDP scanning.
2.2.1 TCP scan
There are three steps to establish a TCP connection between hosts (also called three-way handshake):
(1) The requesting end sends a SYN packet, indicating the destination port to be connected.
(2) Observe the packet returned by the destination:
Return the SYN / ACK packet, indicating that the destination port is in the listening state;
The RST / ACK packet is returned, indicating that the destination port is not listening and the connection is reset.
(3) If a SYN / ACK packet is returned, the requesting end sends an ACK packet to the destination port to complete the 3-way handshake and the TCP connection is established.
According to the steps of establishing a TCP connection, TCP scanning mainly includes two methods:
(1) TCP full connection and semi-connection scanning
The full connection scan establishes a TCP connection with the destination host through a three-way handshake, and the connection will be recorded in the destination host's log file. Semi-connection scanning (also called TCP SYN scanning) does not complete the entire process of TCP three-way handshake. The scanner sends a SYN packet to start a three-way handshake, waiting for a response from the destination host. If a SYN / ACK packet is received, it means that the target port is in the listening state, and the scanner immediately sends a RST packet to abort the three-way handshake. Because the semi-connection scan does not establish a TCP connection, this scan may not be recorded in the log file of the destination host.
(2) TCP covert scanning
According to the TCP protocol, a port in a closed state will respond to a RST packet when it receives a probe packet, while a port in a listening state will ignore this probe packet. According to the different flag bit settings in the detection packet, TCP covert scanning is divided into SYN / ACK scanning, FIN scanning, XMAS (Christmas tree) scanning and NULL scanning.
Both SYN / ACK scanning and FIN scanning bypass the first step of the TCP three-way handshake process and send SYN / ACK packets or FIN packets directly to the destination port. Because TCP is a connection-based protocol, the target host thinks that the SYN packet that the sender should send in the first step has not been sent out, thus defining this connection process error and will send a RST packet to reset the connection. And this is exactly what the scanner needs-as long as there is a response, it means that the target system exists and the target port is closed.
XMAS scan and NULL scan: These two types of scans are just the opposite. XMAS scan sets all flag bits (URG, ACK, RST, PSH, SYN, FIN) in TCP packets, while NULL scan turns off all flag bits in TCP packets.
2.2.2 UDP port scanning
The UDP protocol is a data packet protocol. In order to discover the UDP port being served, the usual scanning method is to construct an empty UDP data packet and send it to the destination port. If a service is waiting on the destination port, the destination port returns an error message; if the destination port is closed, the destination host returns an ICMP port unreachable message. Because UDP port scanning software calculates the number of packets lost during transmission, the speed of UDP port scanning is very slow.
2.3 0S detection
OS detection has a dual purpose: one is to detect the OS information of the target host, and the other is to detect the information of the computer program that provides the service. For example, the result of OS detection is: OS is Windows XP sp3, and the server platform is IIS 4.0.
2.3.1 Binary information detection
By logging into the target host, the OS type and version are learned from the banner returned by the host. This is the simplest OS detection technology.
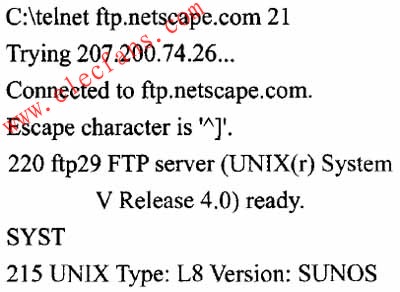
Figure 1 Binary information
As can be seen from Figure 1, after telnet connects to the FTP server, the banner returned by the server has provided server information, and more specific information can be obtained after executing the syst command of ftp.
2.3.2 HTTP response analysis
After establishing an HTTP connection with the target host, you can analyze the server's response packet to get the OS type. For example, the response packet may contain the following information:
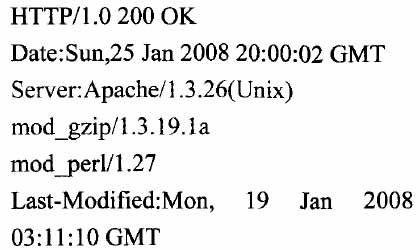
Figure 2 Response packet analysis
From the analysis of the data in the response packet in Figure 2, you can get the server information.
2.3.3 Stack fingerprint analysis
Hosts on the network will communicate with each other through TCP / IP or similar protocol stacks. Because the 0S developer is not unique, the system architecture is diverse, and even the differences in software versions have led to different implementations of the protocol stack. The response to the error packet, the default value, etc. can be used as the basis for distinguishing 0S.
(1) Active stack fingerprint detection
Active stack fingerprint detection is a technology that initiates a connection to the host and analyzes the received response to determine the OS type.
1) FIN detection. Skip the sequence of TCP three-way handshake and send a FIN packet to the target host. RFC793 stipulates that the correct processing is no response, but some OS, such as MS Windows, CISC0, HP / UX, etc. will respond to a RST packet.
2) Bogus logo detection. Some OSes will set the undefined bits of the TCP header in the SYN packet (generally 64 or 128), and some OS will reset the connection after receiving the SYN packet with these Bogus bits set.
3) Statistics ICMP ERROR message. The transmission speed of the ICMP ERROR message is specified in RFCl812. Linux sets the upper limit of target unreachable messages to 80/4 seconds. During the 0S detection, a large number of packets can be sent to a random high-end UDP port, and then the received unreachable messages are counted. OS detection using this technique will take longer because of the large number of packets to be sent and the need to wait for a response. At the same time, packet loss may occur in the network.
4) ICMPERROR message reference. The RFC document stipulates that the ICMP ERROR message refers to the part of the ICMP message that caused the message. For example, for the port unreachable message, some OS returns the received IP header and the subsequent 8 bytes. The ERROR message returned by Solaris refers to more content, and Linux has more than Solaris.
(2) Passive stack fingerprint detection
Passive stack fingerprint detection is a technology that monitors the network, analyzes system traffic, and uses the default value to guess the type 0S.
1) TCP initialization window size. The technique of guessing the OS by analyzing the initial window size in the response is more reliable, because many OSs have different initial window sizes. For example, the initial window size set by AIX is 0x3F25, while the value set by Windows NT5, OpenBSD, and FreeBSD is 0x402E.
2) Don't Fragment bit. In order to improve performance, some OSs set the DF bit in the sent packets, and you can make a rough judgment from the setting of the DF bit.
3) TCPISN sampling. When establishing a TCP connection, the generation of the initial sequence number ISN in SYN / ACK exists regularly, such as fixed, random increase (Solaris, FreeBSD, etc.), truly random (Linux 2.0. *), And Windows uses a time-dependent model , ISN has a fixed increment in each different time period.
2.4 Vulnerability scanning
From the analysis of hacker attacks and the classification of vulnerabilities, the vast majority of scans are conducted for specific network services in a specific operating system, that is, for specific ports on the host. The technologies used for vulnerability scanning are mainly based on vulnerability database and plug-in.
2.4.1 Scanning based on vulnerability database
First, construct a scanned environment model to model and analyze possible vulnerabilities in the system, past hacker attack cases, and the system administrator's security configuration. Secondly, based on the analysis results, a standard set of vulnerable points database and matching patterns are generated. Finally, the program automatically scans based on the vulnerability database and matching pattern. The accuracy of vulnerability scanning depends on the integrity and effectiveness of the vulnerability database.
2.4.2 Scanning based on plugins
The plug-in is a subroutine module written in a scripting language, and the scanner can perform the scan by calling the plug-in. Adding new function plug-ins can enable the scanner to add new functions, or increase the type and number of vulnerable points that can be scanned. You can also upgrade the plug-in to update the characteristic information of vulnerable points, so as to get more accurate results. The plug-in technology makes the upgrade and maintenance of the vulnerability scanning software relatively simple, and the use of a special scripting language also simplifies the programming of writing new plug-ins, making the vulnerability scanning software highly scalable.
2.5 Firewall rule detection
The IP packet analysis method similar to traceroute is used to detect whether a specific packet can be sent to the host behind the filtering device, the purpose is to facilitate the intrusion after the vulnerability scan or the next scan to proceed smoothly. Through this scanning, you can detect the ports opened or allowed to pass through the firewall, and whether the firewall rules allow packets with control information to pass. Further, you can detect the router behind the packet filtering device.
3 Common Vulnerability Scanner
Usually when developing a vulnerability scanning strategy, the scanner will consider the operating system of the program, the technology applied, ease of use, accuracy and other factors. Among them, the usability of the program is the most important and the most basic, but the controllability and accuracy cannot be ignored either.
3.1 Unix / Linux platform
3.1.1 hping
hping supports TCP, UDP, ICMP, RAW-IP multiple protocols. The feature is that it can perform multiple scans such as ping scan, port scan, OS detection, firewall detection, etc., and can customize the ICMP / UDP / TCP packets sent to the target address and display the response information.
3.1.2 icmpush & icmpquery
The characteristic of icmpush & icmpquery is that the ICMP protocol is fully applied, and the structure and types of ICMP packages can be customized. Scanners can use this tool to find out all the subnets of the target network, so that they can scan a few specific subnets ignoring the broadcast address.
3.1.3 Xprobe 2
It is a professional port scanning and OS detection program. The feature is that its own 0S feature database is detailed, and the reliability of OS detection is better.
3.1.4 THC-Anap
OS detection program. The characteristic is that the scanning speed is fast and the scanning result is reliable.
3.1.5 Whisker
Vulnerability detection program for CGI. The multi-thread and multi-file scanning technology is applied, the database of vulnerable points is updated frequently, and the scan results are reviewed on their own, so that the scan results have good reliability.
3.1.6 Nessus
Vulnerability detection procedures. The application of active scanning and high-speed scanning technology can set the scanning process. The characteristic is to support the DMZ zone and the large-scale scanning of the multi-physical partition network.
3.1.7 Firewalk
Firewall detection program. Use the technology similar to traceroute to analyze the response of the IP packet to determine the firewall's access control list and draw the network topology map.
3.2 Windows platform
3.2.1 Pinger
Is a graphical ping scanning tool. The feature is that you can specify the IP address to be pinged, display the scan result in the form of a graph, and save it to a text file.
3.2.2 Fport
It is a port scanner. The characteristic is that the scanned port can be matched with the program using the port, the scanning speed is fast, and the matching degree is good.
3.2.3 SuperScan
Can carry out ping scan, port scan, 0S detection, and a leucorrhea Trojan port list, you can detect whether the target computer has a Trojan.
3.2.4 GFILANguard
Vulnerability detection procedures. The characteristic is that it integrates network auditing and patch management functions, and can automatically generate network topology map and automatic patch management.
The above vulnerability scanning procedures and characteristics are shown in Table 1.
4 Conclusion
Generally speaking, a comprehensive application of multiple scanning methods or scanning procedures can obtain relatively satisfactory results. However, vulnerability scanning is analyzed from its technical principles and has side effects that cannot be ignored. For example, a certain scan of a large range of IP addresses or ports, repeated high-speed specific connection request, the result is that there are a large number of connection request packets on the target network and the host, which can cause network congestion and the host cannot be used This is exactly the method and performance of DoS attacks. Therefore, to prevent vulnerability scanning and possible DoS attacks, the following three points should be achieved:
1. Use strict filtering rules on firewalls and filtering devices to prevent scanned packets from entering the system.
2. In addition to the necessary network services, the host system prohibits other network applications.
3. For network services that are only open to the inside, change the ports that provide services.
In addition, the data sent during the network scan will more or less contain the scanner's own relevant information, so that it can also capture the data packets during the scan and trace the scanner back, which is also a worthy research direction.
MOSO provide Dim-to-off Led Driver for energy-saving and circuit safety, supporting 0-10V, PWM, timer step dimming or DALI control, with low stand-by power. It is IP67, build-in surge protection, Class II design, power range 75W~320W. Dimming driver can adjust the output by programming software or controller which is isolated with diming signal.


This Dimming driver ensures cool operation and long life with extruded-metal housing and fully glue-potted. It is certified by CCC, CE, TUV, ENEC and CB standards, widely used in street lighting, flood lighting, industrial lighting.
MOSO has set several distributors in Europe, United States, Latin America, Asia and Australia. All MOSO Dim-to-off Led Driver provide 5 years global warranty. In case of any failure, customers can get replacement either from MOSO directly or any one of MOSO distributors.
MOSO always dedicates to providing professional outdoor lighting solutions. Please feel free to contact our sales team if you need any support!
Dim-to-off Led Driver
Dim-to-off Led Driver,Dim-to-off LED Dimmable Driver,Dimmable Dim-to-off LED Driver,Dim-to-Off Timer Dimmable LED Driver
Moso Electronics , https://www.mosoleddriver.com
